Recent developments in cybersecurity have unveiled a concerning trend in online fraud, notably a sophisticated phishing campaign targeting Booking.com customers. Using a deceptively clever tactic, cybercriminals harnessed the Japanese hiragana character “ん” to create URLs that closely mimic legitimate links, providing a false sense of security to unsuspecting users. This attack exemplifies how attackers exploit visual similarities between characters to deceive individuals into clicking malicious links, ultimately leading to the installation of malware. The cyber landscape is becoming increasingly complex, requiring heightened awareness and vigilance on the part of users to avoid falling victim to these schemes.
Understanding Phishing: A Persistent Threat to Online Travelers
Phishing remains one of the most prevalent forms of cybercrime, specifically tailored to compromise personal and financial data. As the online travel industry flourishes, platforms like Booking.com, Expedia, and Airbnb have become prime targets for these scams. The ease of online booking and the trust users place in these services make it essential to educate potential victims about what phishing entails.
Phishing is fundamentally a form of social engineering, where attackers seek to trick victims into revealing sensitive information by masquerading as a legitimate entity. This can happen through various channels, including email, social media, and direct messaging. The available tactics are numerous, ranging from spear phishing, which targets specific individuals or organizations, to broader phishing campaigns aimed at capturing a high volume of unsuspecting users.
- Email Phishing: The most common method where fraudulent emails stimulate action, typically urging the recipient to click a link.
- Smishing: Uses text messages to lure victims, often directing them to phishing websites.
- Voice Phishing: Phone calls meant to extract information directly from victims, claiming to be from legitimate organizations.
Even established companies like Booking.com, which is essential for travelers seeking accommodations, are not immune to phishing attacks. The recent case employing the “ん” character underlines how attackers can replicate the appearance of legitimate websites, challenging basic security measures implemented by users.
The Role of Homoglyphs in Phishing Attacks
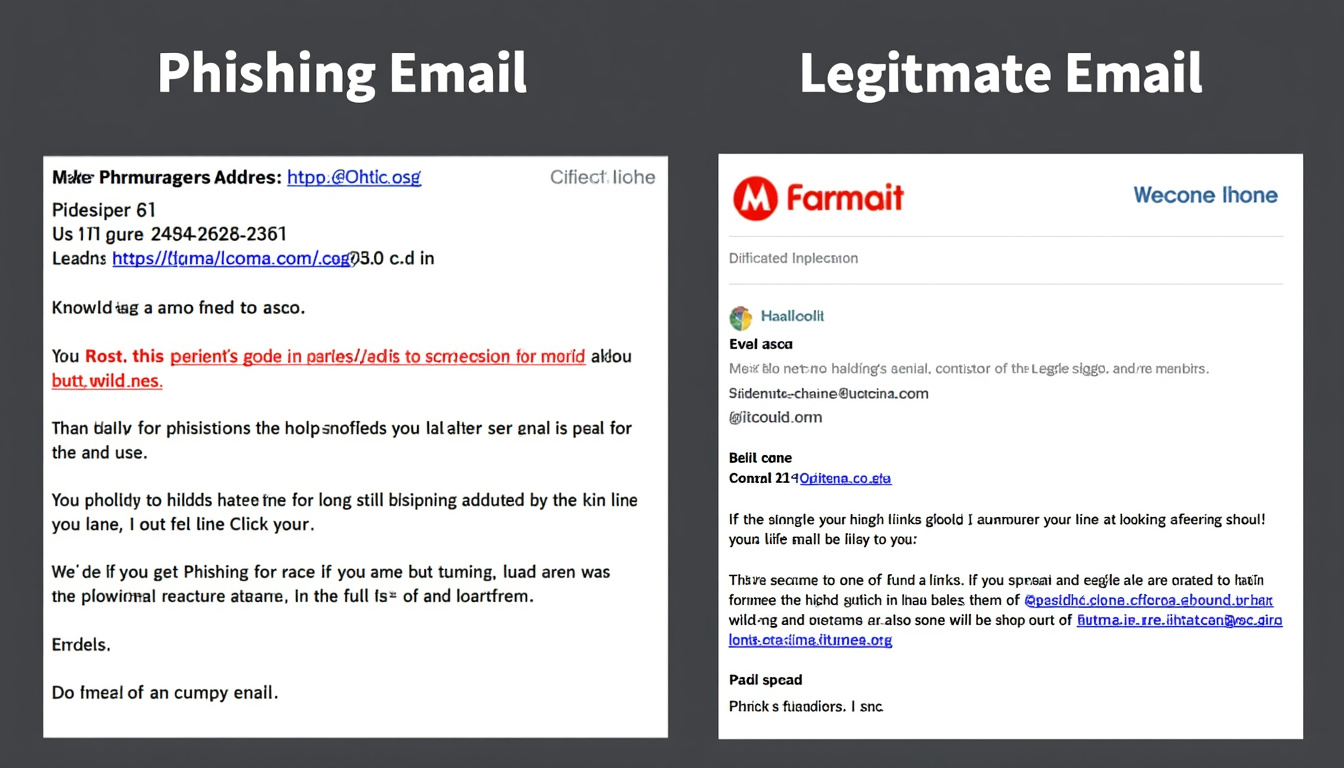
At the heart of this particular phishing attack lies the concept of homoglyphs—characters that appear visually similar but belong to different character sets. In the case of Booking.com, the Japanese character “ん” was used to replace the Latin characters, allowing scammers to craft fraudulent URLs that closely resemble the actual site. This specific tactic causes confusion, especially when viewing links at a glance.
Homoglyphs exploit the human eye’s tendency to overlook subtle differences. Many legitimate domains, including popular ones like Hotels.com, Trivago, and Kayak, become vulnerable to these attacks. For example, an attacker might create a link that appears to be from Booking.com yet hides malicious intent. Users frequently do not reflect on the URL provided in emails or messages; hence, they might easily misjudge its authenticity.
Consider the implications of such an attack in practical terms: a victim receives an email that appears to be from Booking.com, urging them to update account details. The link, although appearing legitimate, redirects them to a phishing page set up to steal their login credentials. Understanding this allows users to heighten their scrutiny of URLs, particularly when they look suspicious.
| Homoglyph Examples | True Character | Homoglyph Character |
|---|---|---|
| O | Latin Capital Letter O | Cyrillic Capital Letter O |
| A | Latin Capital Letter A | Greek Capital Letter Alpha |
| l | Latin Small Letter L | Greek Small Letter Lambda |
In sum, it is vital for users to differentiate between various character sets when dealing with online communications. The confusion created by these tactics emphasizes the importance of user education and awareness about how sophisticated phishing campaigns can operate. The alarming potential for financial loss or data theft cannot be overstated, especially in a time when online bookings constitute a major component of the travel industry’s ecosystem.

The hopes of a family eagerly anticipating a holiday can quickly turn sour when faced with unexpected challenges. In a recent incident involving a family who paid €1,800 for what they believed to be a charming seaside home in Galicia,…

Rent a Piece of History: Stay in the Guest House of Derek Jeter’s Former Upstate NY Castle on Airbnb
For those looking for a unique getaway, the opportunity to stay in the guest house of former baseball superstar Derek Jeter’s historic estate is now a reality. Nestled in the picturesque Hudson Valley, the guest house at Tiedemann Castle, once…
Dissecting the Recent Booking.com Phishing Attack
The recent phishing scam targeting Booking.com is a stark reminder of the lengths cybercriminals will go to mislead individuals. As reported, security researcher JAMESWT first identified this attack, which utilizes specific characters that resemble traditional URL slashes, making fraudulent links attractive to the unsuspecting eye.
This particular attack relies on the visual misrepresentation of the hiragana character “ん,” which may not be easily discernible in all fonts. When incorporated into links, this character can mimic the appearance of valid URL sequences like “/n” or “/~.” Consequently, victims may find themselves entering their credentials on a malicious site, completely unaware until it is too late.
This tactic denotes a strategic shift in phishing attacks, where advanced techniques are employed to develop more credible-looking counterfeit sites. Such measures necessitate a robust examination of URLs, particularly focusing on the location of critical characters such as “ん.” For instance, an example phishing URL would appear as:
https://admin.booking.com/hotel/hoteladmin/… but truly leads to: https://account.booking.comんdetailんrestric-access.www-account-booking.com/en/
In reality, most victims remain unaware of the intricacies behind such attacks and often overlook the fact that the actual registered domain does not match the perceived link. This lack of vigilance can lead to devastating outcomes, including identity theft and financial loss.
- Monitor email sender addresses: Often attackers will spoof addresses to appear legitimate.
- Hover over links: Before clicking, check the actual URL that appears.
- Use security software: Employ endpoint security to mitigate risks from malware.
Consequences of Falling for Phishing Attacks
The consequences of falling victim to phishing attacks can be significant. Modern phishing scams not only affect individual users but can also compromise entire businesses, resulting in extensive reputational damage. In the case of Booking.com, such breaches could diminish user trust in the platform, impacting broader customer relations.
For example, once attackers gain access to credentials, they can infiltrate a user’s subsequent accounts across various platforms, including financial services, other booking sites like Agoda and Priceline, and email services. This cross-platform vulnerability heightens the stakes for victims, showcasing the interconnected nature of online security.
Moreover, compromised user data often leads to financial consequences beyond just direct theft. Victims may incur costs associated with credit monitoring or identity recovery services following an attack. The scope of penalties impacts not just individual users, but also the companies who host those accounts. Major cybersecurity liability issues can arise in the wake of successful attacks, placing legal burdens on organizations to safeguard their networks and customer relationships.
| Potential Consequences | Direct Impact | Long-term Effects |
|---|---|---|
| Financial Loss | Theft of funds through fraudulent transactions | Loss of trust in financial institutions |
| Data Breach | Exposure of personal information | Legal consequences for companies involved |
| Identity Theft | Malicious use of stolen identity for illicit activities | Rebuilding one’s digital reputation |
With the stakes so high, it is evident that businesses and users alike must adopt a proactive approach to web safety. Establishing robust security measures is only as effective as users’ engagement in their security. By understanding the methods used by attackers, including the exploitation of visual character similarities, both individuals and organizations can develop better strategies for defense.
New York City has long been a bustling hub for tourism, drawing nearly 63 million visitors in 2024, which generated over $74 billion in economic impact. The city stands as the second-largest tourism market globally, following only London. Amidst this…

Les plateformes de location de vacances ont connu une transformation majeure, offrant des alternatives flexibles à l’hébergement traditionnel. Cependant, cette évolution rapide présente des défis importants, notamment en matière de sécurité et de confiance. L’anonymat des transactions en ligne expose…
Taking Steps to Safeguard Against Phishing
In light of the recent phishing attacks, users are urged to implement comprehensive strategies for safeguarding personal and financial information. Given that platforms like Booking.com and Hotels.com serve millions of clients daily, the onus is on users to remain alert and informed about potential threats.
1. Verification of Links: Before clicking on any link, always hover over it to reveal the actual destination. This simple action can often uncover deceptive URLs that incorporate homoglyphs.
2. Using Two-Factor Authentication: Enabling two-factor authentication (2FA) for accounts adds an extra layer of security, making it challenging for attackers to gain access even if they obtain login credentials.
3. Keep Software Updated: Regular software updates often fix security vulnerabilities. Whether it’s an operating system, browser, or security suite, ensuring that everything is current can protect you from known exploits.
4. Educate Yourself and Others: Knowledge is one of the best defenses against phishing. Being aware of common tactics used by cybercriminals can prepare users for potential schemes.
5. Report Suspicious Activity: If any phishing attempts or rogue activity are noticed, report them immediately to the relevant company or authority. This helps in building a collective defense against such malicious attacks.
- Utilize Security Tools: Employ comprehensive security suites that include email filtering, malware protection, and link scanning.
- Be Cautious with Public Wi-Fi: Avoid accessing sensitive sites on public networks to mitigate risks.
What Businesses Can Do
It’s vital for businesses, especially those in the hospitality sector, to take proactive measures to protect themselves and their customers. This means maintaining high levels of website security, conducting regular audits for vulnerabilities, and educating staff on phishing detection.

Airbnb is set to appeal a federal court decision that upheld stringent regulations regarding short-term rentals in New Orleans, marking an important chapter in the ongoing debate between municipal authorities and online rental platforms. Recent rulings have been pivotal in…

New Orleans City Council Achieves Significant Victory in Legal Battle Against Airbnb
The recent legal battle between the New Orleans City Council and Airbnb has unfolded dramatically, with significant implications for short-term rental regulations and the broader hospitality industry. On September 8, 2025, the U.S. District Court for the Eastern District of…
Conclusion: A Call to Action for Vigilance and Awareness
In a constantly evolving digital landscape, both individuals and businesses must enhance their defenses and stay informed about the latest phishing tactics. With the sophistication of attacks like the recent Booking.com phishing campaign, it is indispensable to develop habits that prioritize security. From understanding the implications of homoglyphs to recognizing the importance of careful link scrutiny, knowledge is empowerment.
Success lies not only in technical solutions but also in nurturing a culture of awareness where everyone learns to adhere to best practices. By integrating these strategies, it becomes feasible to navigate risks effectively, sustaining trust in digital platforms within the travel industry and beyond.

Location de vacances : astuces pour échapper aux sanctions contre Airbnb
Les locations de vacances à travers des plateformes comme Airbnb sont devenues l’une des tendances majeures du secteur du tourisme. Cependant, avec l’essor de cette pratique, les réglementations ont aussi augmenté, et de nombreuses villes instaurent des lois pour réguler…

Booking Holdings Places Its Strategic Bet on Agentic AI to Compete with Tech Giants
With the ever-evolving landscape of the travel industry, Booking Holdings is making bold moves to ensure its position remains at the forefront of innovation. The recent focus on agentic artificial intelligence demonstrates the company’s commitment to enhancing user experiences and…
