The hospitality sector is increasingly facing threats from sophisticated cyberattacks, particularly through phishing campaigns that exploit trust in legitimate platforms. A recent wave of malicious emails mimicking Booking.com has captured attention within cybersecurity communities. Researchers from Cofense Intelligence have reported a significant uptick in these dangerous phishing schemes, primarily targeting hotel staff and personnel involved in managing bookings. These attacks leverage social engineering tactics to deceive recipients into downloading malware that can disrupt operations and compromise sensitive data.
Understanding the ClickFix Phishing Scheme
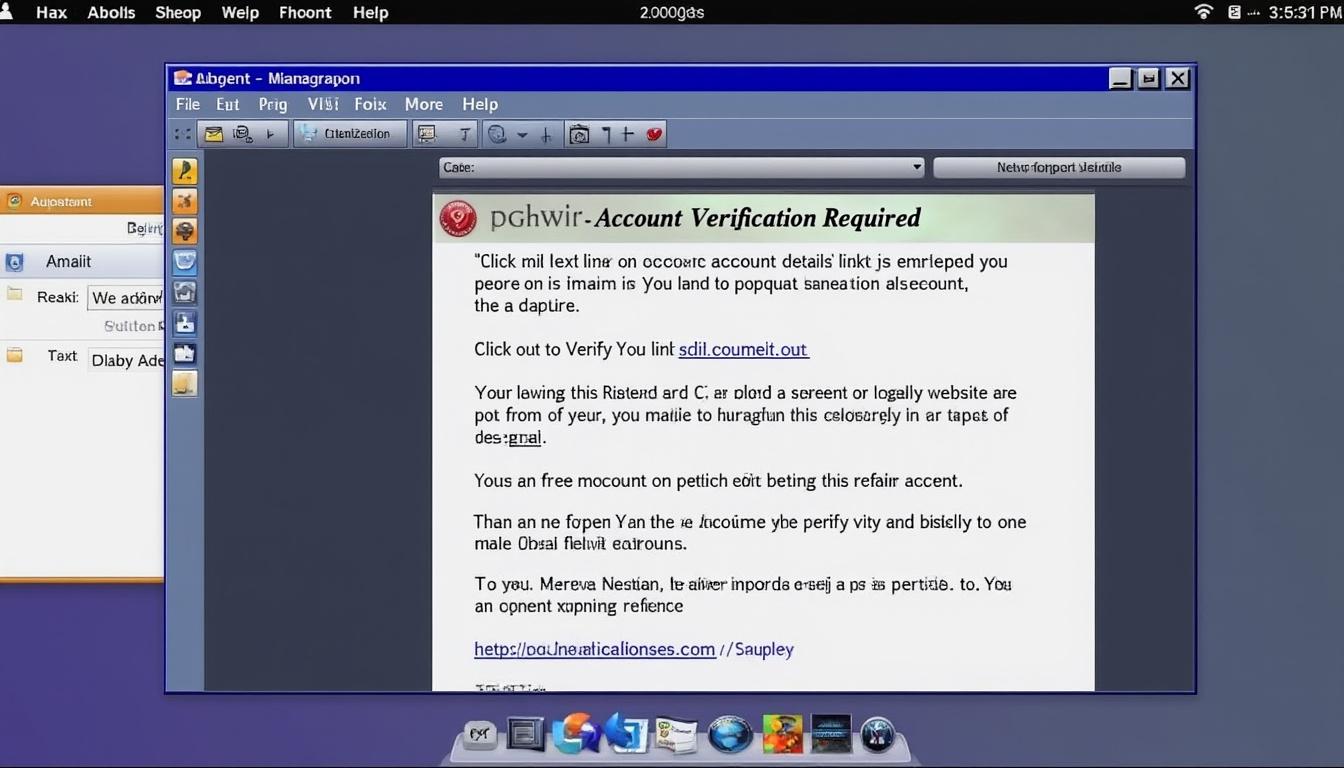
The core methodology behind this phishing campaign is the use of a deceptive CAPTCHA system known as ClickFix. Launched in November 2024, the campaign peaked in March 2025 and accounted for astounding 47% of its total activity during this time. It exploits a well-known anxiety among hotel staff regarding customer service and reservations, compelling them to act swiftly without due vigilance.
How ClickFix Operates
ClickFix operates through a fairly sophisticated mechanism that leads victims to believe they are performing a legitimate action. When hotel staff receive these spoofed emails, they are presented with a request to either confirm a reservation or address a guest’s issue. Central to these emails is a link directing them to a counterfeit CAPTCHA page. Here, victims are misled into executing a malicious script that compromises their Windows devices.
- Phase One: The recipient receives an email that appears authentic.
- Phase Two: They click on a link that leads to a fake CAPTCHA site.
- Phase Three: The site prompts them to run verification steps which enable malware installation.
The phishing emails cleverly exploit the urgency associated with customer service interactions, often including threats of reputational damage if immediate action is not taken. By creating a façade of legitimacy, cybercriminals gain the trust of their victims, allowing malware to infiltrate hotel management systems unnoticed.
| Steps of ClickFix Operation | Description |
|---|---|
| Email Spoofing | Fake Booking.com emails requesting urgent actions from hotel staff. |
| CAPTCHA Page | Redirects users to a counterfeit CAPTCHA page that initiates malware download. |
| Script Execution | Victims unknowingly run a script by following on-screen instructions. |
As a result, many unsuspecting hotel staff have inadvertently transformed their devices into vulnerable points of access, serving as gateways for malicious software to proliferate within hotel systems.
Types of Malware Distributed through Phishing Campaigns
The primary goal of these phishing campaigns targeting the hospitality industry is to distribute various types of malicious software. According to analyses conducted by cybersecurity experts, 53% of the malware associated with the ClickFix campaign pertains to Remote Access Trojans (RATs) such as XWorm RAT. Other prominent threats include the Pure Logs Stealer and DanaBot, which aim to extract sensitive information from compromised systems.
Consequences of Malware Infiltration
Successful infiltration of these malware strains can yield disastrous outcomes for hotels, including:
- Data Breaches: Sensitive customer data, including payment information and personal identification details, may be exposed to identity theft.
- Operational Disruption: Malware can slow or shut down hotel management systems, affecting operations.
- Legal and Reputational Damage: Cybersecurity breaches can lead to legal repercussions and a loss of consumer trust.
Given that the hospitality sector is primarily concerned with customer satisfaction, downtime, or disruptions caused by malware can have far-reaching negative effects. The interlinked nature of hospitality services makes it especially imperative for hotels to maintain robust email security measures to mitigate such risks.
| Malware Type | Impact |
|---|---|
| Remote Access Trojans (RATs) | Provide unauthorized access to attackers, enabling them to control infected systems. |
| Information Stealers | Extract sensitive information such as login credentials and credit card numbers. |
| Keyloggers | Track user inputs to capture passwords and sensitive data in real-time. |
Hotels must assess their current cybersecurity strategies to effectively address these threats and safeguard themselves from becoming victim to the ongoing ClickFix phishing operations.
Recognizing Phishing Attempts
Understanding the signs of phishing attempts is crucial for safeguarding against these attacks. As phishing attacks grow increasingly sophisticated, hotel staff must be educated about identifying potential threats. Recent phishing emails from the ClickFix campaign have included various telltale signs that indicate their fraudulent nature.
Common Signs to Watch For
Some of the red flags associated with phishing emails include:
- Urgent Language: Wording that emphasizes immediate action, such as “urgent request” or “response needed within 24 hours.”
- Unfamiliar Email Addresses: Email addresses that appear suspicious or do not match the standard format of Booking.com.
- Hyperlinks: Links that mislead users by displaying a legitimate URL while redirecting them to counterfeit sites.
By equipping hotel staff with knowledge about these signs, organizations can effectively reduce the likelihood of successful phishing attempts. Reputable organizations, including Booking.com, are continuously working to improve their cybersecurity measures. They urge employees to verify the authenticity of any communication before taking any action.
| Phishing Indicators | Recommended Actions |
|---|---|
| Unusual Requests | Confirm requests through official channels before taking action. |
| Excessive Urgency | Assess the necessity of immediate action; genuine requests typically allow time for response. |
| Multiple Links | Hover over links to check the true destination before clicking. |
Such preventive measures can make a significant difference in the organization’s overall cybersecurity posture, especially in a landscape rampant with identity theft and cyber fraud.
Painting a Holistic Picture of Email Security
To effectively combat phishing threats, hotels must adopt a holistic approach to email security. This involves evaluating prevailing protocols and integrating new technologies to bolster defenses against emerging threats. A multifaceted strategy combines employee training, updating software, and implementing strong cybersecurity policies.
Key Components of an Effective Email Security Strategy
An effective email security strategy comprises various elements that work synergistically to deter cyber threats:
- Awareness Training: Regular training sessions educating staff on malware threats and identifying phishing attempts.
- Regular Software Updates: Keeping all security software, including anti-virus programs, up to date to combat vulnerabilities.
- Incident Response Plans: Having a structured protocol in place to respond to and resolve cybersecurity incidents swiftly.
Furthermore, investing in advanced technology can help identify and thwart phishing attempts before they reach employees. Solutions powered by artificial intelligence can scan emails and flag suspicious activity, ensuring enhanced online safety for hotel operators.
| Components of Email Security | Description |
|---|---|
| Training Programs | Help employees recognize and deal with potential phishing threats effectively. |
| Latest Technology | Implement AI-driven tools that enhance the capacity to spot malicious emails. |
| Security Protocols | Establish secure methods for handling sensitive client information and communications. |
By leveraging these strategies, hotels can effectively minimize the risk of falling victim to phishing scams posing as reputable organizations like Booking.com.
Real-world Impact of Phishing on the Hospitality Industry
The implications of phishing attacks can extend beyond immediate operational issues. Understanding the broader impact of these cyber threats on the hospitality industry highlights the necessity for vigilance. A case study of recent phishing attacks reveals how unprepared hotels faced significant repercussions.
Case Study: Reservations Compromised
In one notable incident, a hotel unknowingly fell victim to a phishing scheme that linked back to spoofed Booking.com emails. Upon responding to a fraudulent communication, employees inadvertently gave attackers access to their booking system. This breach resulted in unauthorized changes to guests’ reservations, prompting customer complaints and ultimately harming the hotel’s reputation.
- Diminished Customer Trust: Frequent phishing incidents can result in guests questioning the safety of their information.
- Increased Operational Costs: The hotel faced heightened costs to rebuild trust, including marketing campaigns and increased cybersecurity measures.
- Revenue Loss: Poor customer experience directly correlates to revenue decline, as dissatisfied guests seek alternative accommodations.
This incident reaffirms the pressing need for hotels to not only adopt strong cybersecurity measures but also to continually assess and adapt their strategies to stay ahead of evolving threats.
| Impact of Phishing | Effect on Hotel Operations |
|---|---|
| Customer Data Exposure | Loss of sensitive information can lead to identity theft risks for customers. |
| Reputational Damage | A decline in public perception can adversely affect booking rates. |
| Recovery Costs | Expenses related to enhancing cybersecurity can strain budgets. |
The harsh realities of phishing demonstrate that the consequences extend beyond the immediate impact, reinforcing the necessity for a comprehensive approach to cybersecurity within the hospitality sector. Organizations must not only react to threats but anticipate them through proactive measures.
